Following the recent hacking of the email account of Hillary Clinton’s campaign chairman John Podesta, the Democrats (along with the media) have been on an anti-Russia crusade. For Russia’s alleged part in the hack, the US government is contemplating whether or not to launch covert cyber attacks against the Kremlin.
When Vice-President Joe Biden was asked in a recent interview, “Why haven’t wesent a message yet to Putin?” he responded, “We’re sending a message [to Putin], it will be at the time of our choosing, and under the circumstances that will have the greatest impact.”
NBC also reported earlier this month that the White House has asked the CIA to deliver options for a wide-ranging “clandestine” cyber operation designed to harass and embarrass the Kremlin. This rhetoric is similar to that which was spouted prior to the bombing of Pearl Harbor in 1941.
From 1931 onward, tensions between the Japanese and Americans began rising over Japan’s military expansion in the Pacific. Following the Japanese invasion of French Indochina in 1940, the US placed an embargo on oil exports to Japan and froze its assets. As the Japanese began to run low on oil reserves, the embargo forced them to respond, resulting in the attack on Pearl Harbor.
Although tensions existed between the US and Japan, nobody expected that just one day after FDR penned a letter to Emperor Hirohito appealing for amity between the two nations, His Majesty’s forces would leave a US naval base in smoking ruins. Similarly, cyber attacks can be conducted from the comfort of a control room and could literally materialize overnight without any advance warning.
So, given the near certainty that cyber attacks are only going to escalate, what would a potential Cyber Pearl Harbor look like?
21st Century Warfare
Let’s start with the most obvious and easy target: the Internet itself.
A week ago, a cyber-attack on online hosting company Dyn took down websites such as Twitter, Netflix, Airbnb, and PayPal. Hackers were able attack the company’s network by infecting 6.4 billion “smart” devices such as printers and webcams that are now ubiquitous in America. The perpetrators then used the infected devices to inundate Dyn with over 300 gigabytes per second of traffic, causing the company’s servers to crash.
This map shows the massive outage hotspots as a result of the attack.
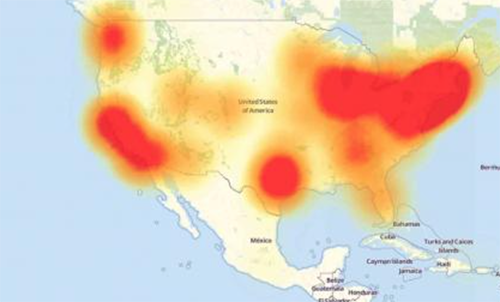
Source: http://downdetector.com/status/dyn
The Dyn attack exposed a huge problem of today’s interconnected world: All the “smart” TV’s, toasters, and even toothbrushes can be hacked and used in a cyber attack. Another recent example is the hacking of Internet-connected baby monitors. Hackers were able to watch small children—and even talk to them—from half a world away.
So, if hackers were to take down multiple hosting servers for a prolonged period of time, what would be the impact on online giants like Amazon, Netflix, and Uber? There would be no Google searches, Uber outings, or European Expedia excursions. Considering these companies are some of the biggest in the world, it would have huge implications for their suppliers and the global economy.
Virtual businesses of all kinds would have to cease operations. Likewise, the online trading platforms, which now provide the backbone for over 90% of all US stock trades, would face similar issues. What do you think your odds are for getting through to a live broker at an online trading firm in the midst of a cyberattack-induced panic?
The Internet, however, wouldn’t be the only target in a cyberwar. Critical infrastructure is also susceptible to cyber attacks.
A Shot to the Heart
As in conventional warfare, critical infrastructure will be a major target. There have been multiple recent examples of hackers taking down infrastructure.
In December 2015, hackers took down about one-third of Ukraine’s power stations, knocking out power to almost 250,000 people. Even though the outage only lasted about 12 hours, it resulted in major disruptions across the country.
One of the most sophisticated cyber attacks came in 2010, when hackers released a piece of malware called Stuxnet into the Iranian nuclear power system. This attack destroyed over 25% of its centrifuges. This happened in spite of the fact that facility was in tight lockdown… its computers were not even connected to an external network.
Another potential target is nuclear systems. These could be infected by a cyber virus. However, a nuclear meltdown emanating from a cyber attack is unlikely in the US. This is due to the Nuclear Regulatory Commission’s requirement that critical safety and security systems be isolated from the Internet.
If a virus like the one found in the Iranian nuclear plant was found in a US power station, it would have to be temporarily closed until the virus was removed. That is the best case scenario. There is also the possibility the virus could embed itself so deep in the system that restarting the generators could lead to disaster.
Given that nuclear energy accounts for 20% of US power generation, and people want the lights to come on at night, an outage could cause energy prices to skyrocket.
Water treatment facilities have also been the target of recent cyber attacks. If hackers were able to alter the chemical balance injected into the water supply in treatment facilities, it could poison the population of an entire city. People would be unable to drink or bathe in the water until the whole treatment system had been completely cleaned out.
Although there hasn’t been a successful hack on major infrastructure in the US thus far, a 2014 report ICS-CERT found that over the previous 12-month period, critical US infrastructure had been the target of at least 245 cyber attacks. So, what impact could a serious cyber attack on the US power grid have?
The Trip Switch
Some of what follows may feel a bit dystopian. But that doesn’t mean we shouldn’t take a moment to ponder the potential havoc caused by a prolonged power outage in the US.
In a power outage, severe winter conditions in the North or a summer heat wave in the South would quickly make these places unlivable… at least temporarily until the infrastructure could be restored.
In addition, America’s reliance on a “just in time” (JIT) inventory strategy, a system developed by Toyota in the 1970’s, could be broken. The JIT strategy focuses on ordering and receiving goods only as they are needed, thus reducing waste and inventory costs. If disruptions in the supply chain occurred, it could quickly result in shortages akin to those seen ahead of major hurricanes.
Even if food did manage to reach the cities, how could produce, dairy products, and meat be preserved safely?
In addition, the supply line for medicines is equally thin. That means in the event of a protracted cyber war, critical medicines could simply be unavailable at any price.
One thing is certain: people in areas affected by a power outage would be very reluctant to venture out at night. With crime levels elevated in cities such as St. Louis and Baltimore (both in the world’s top 20 most dangerous cities), a prolonged grid outage could create chaotic scenes reminiscent of The Purge: Anarchy, in which law and order gives way to rampant crime.
The situation in larger cities (such as New York and New Orleans) may be no better given the chaos that ensued during the power outages associated with Hurricane Katrina and Hurricane Sandy.
Lack of heat and food plus an uptick in violence would lead to injuries as well as fatalities. As a result, hospitals would be inundated with patients. But, given that most hospitals only have backup power to last around 72 hours, what would happen during an extended power outage?
As if a prolonged power outage wasn’t scary enough, the possibility of cyber attacks on commercial aircraft and military equipment is also real.
Cyber Hijack
Coincidently, the evening before I put pen to paper on this article, I sat down for dinner with a well-known and very experienced engineer and software entrepreneur. I mentioned to him that I was writing this article and wanted to pick his brain about how far cyberwarfare could go. In other words, what can be hacked as a potential target?
I asked him about the possibility of cyber attacks on aircraft, a cyber version of the tragedy of 9/11.
“Commercial aircraft have already been hacked. In fact, Boeing and Airbus both have built-in systems which allow their aircraft to be remotely controlled, they just don’t want you to know that.”
My dinner companion is not the only one concerned about aircraft being hacked.
A 2015 report from the GAO found it’s possible for someone with just a laptop to commandeer an aircraft, take over both the flight warning and navigation systems, and put a virus into flight control computers.
Along with aircraft being a potential target, air traffic control towers can also be hacked. The British Aviation Authority recently issued a safety alert over the rising number of hacks on air traffic control transmissions. So far in 2016, there have been 20 such incidents; in 1998, there were just three.
Given these facts, if a cyberwar did break out and commercial aircraft were targeted, it would certainly bring all air travel to a grinding halt. This would have a massive effect on the global economy, similar to the disruptions caused in the days post 9/11.
Military aircraft could also be targeted in cyber attacks. Boeing is already helping the US Air Force turn old F-16 fighter jets into drones. Given that the blueprints for the Air Force’s new F-22 and F-35 jets were stolen by Chinese hackers, the intricate workings of these jets must be known. This gives rise to the possibility of a hack with deadly consequences.
With almost all modern equipment being the potential target of a cyber attack, what are some of the important signs to pay attention to as this new method of warfare plays out?
Cyber Warning Signs
Although many of the potential scenarios I have outlined may seem far-fetched, the same could have been said in the 15th century before artillery barrages changed the landscape of warfare. Or in the 20th century, just before Polish cavalry tried to charge down a division of German panzers. There is no doubt that cyber attacks, dubbed ‘’the fifth-element of warfare,’’ are a game-changer.
Given the amount of cyber activity and probing that is going on from all sides, how do we effectively tune out the noise and focus on the real risks?
Although the hacking of email-accounts has garnered much attention in the media, the real threat lies in the hacking of infrastructure or military equipment. Cyber attacks have democratized the act of war, and the potential for escalation is huge. If an infrastructure or commercial aircraft hack were to result in casualties, America’s hand would be forced… just as Japan’s was in 1941. All bets would be off.
There is no doubt the US government is taking the threat of a major cyber attack seriously. Otherwise, they wouldn’t be spending $16 billion on cybersecurity this year. While no one can predict when a black swan event like a Pearl Harbor may occur, it is nonetheless important to consider the possibility that at any moment the lights could literally go out on the status quo.
While we can hope nothing will come to pass, that seems a faint hope. Therefore, it’s important to take at least the basic preparations against a sudden cyber war… just as you would if you live in an area susceptible to hurricanes or earthquakes.
Stephen McBride
Chief Analyst, RiskHedge




